By : Prof
Charles Severance (DR Chuck)www.coursera.org
* The research networks that were funded by the U.S., Department of Defense, the ARPANET. At meet the mid-80s, the ARPANET sort of came out into the academic world first, and then the rest of the world, in '89, '90. And then, also, '89, '90, the next sort of step is the creation and then distribution of the World Wide Web, which
really is, sort of, throughout the'90s.
* The internet and web took off in the outside the academic sector in 1994
* In the mid 90's, the internet wasn't nearly as fancy and as important as it is now, so it was really easy to find these people and they were always happy to talk : Tim Berners-Lee, James Wells
* Tim Berners-Lee is the inventor of the world wide web
* James Wells is one of the founders of the real audio. over 700 thousand people who have downloaded the player in a last six months at a rate of 250,000 per month, so if we just do the arithmetic you will imagine that over the next six months, there would bemany millions of people listening and tens of thousands of people producing. It allows the idea of what we call narrow casting. That is to take information in a very inexpensive way and get it to very specific points of interest and targets. Another large user of RealAudio is education. James Wells has this imagination that we could squeeze teaching down into little tiny audio and people can take audio classes all around the world. * Modem : in 1993 94 95 we used 28 kilobit modems* Dr Chuck created Sync-O-Matic in 1996 (couldn't send video. We could only send audio because the connections were so slow back, but can send slide and audio)* 1999 : Dr Chuck invented Clip Board to Apple but Apple disin't take it, can actually draw on, slide, and you could flip the slide back and forth and you have a pointer and you can type text on the slider make a blank thing
* DR Chuck was the chief architect of Sakai : learning management system (can plug material like recorded lectures).
#In 2007 - 2012 : he built standards with IMS.
#2012 : COURSERA !!
* Alan Turing is known as the father of modern computer scientists. And in the 1930s and 1940s he was a mathematician who developed foundational notions like what does computation mean. Very early in his career,
shortly after he graduated his PhD from Princeton, he went to Cambridge and then Bletchley Park as World War out. The problem was that the war machines need to communicate, so it had to increasingly use wireless
communication so that their activities will be highly coordinated. The problem with wireless communications is that, everyone can put up an antenna and listen. And so you had to come up with some tricky way to describe or to capture what it is that you were talking about. And encrypt it so no one could see it. If you could break the encryption then you could see what the opponent was thinking. This became quite valuable in particular to the British government to be able to break the initially German codes. Because then they could anticipate and
there was a lot at stake for all sides. 10,000 people solving this one problem. Breaking German cryptography was so difficult and so challenging that money was no object and technology was no object. The Bombe, which is a
mechanical computer that rotates with contacts and electrical wires and tries to guess the combinations for the
German enigma machine. It goes as fast as it possibly can, so that it can do millions of checks per second. And it
stops when it thinks it's got a good one. And then, as the war progressed, the German cryptography got better and better and better. And so, they had to develop a new machine. But a mechanical machine could not, they couldn't make it go faster. They made kind of the fastest mechanical machine they could. So they had
to solve the problems of creating an electronic computer. And so they created this computer called the Colossus.
The Colossus decrypted these more complex messages. The Germans never guessed that they're code had been broken. And by the end of the war the, it was said that the intelligence people at Bletchley Park often had a de-crypted version of the military message before the actual German commander had that copy of the message.
The video of Alan Turing was taken based on the 100th. Anniversary of Alan Turing's birth which was June 2012.
- Bletchley Park, just north of London, inbetween Cambridge and Oxford, was considered by many as the birthplace of modern computer science ; Bletchley Park was an early version of a multidisciplinary
science center, much like CERN or NCSA is today. Many brilliant people, with different skills and backgrounds were brought together to solve difficult problems.
- Alan Turing lulus dari Princeton th 1938, setelah dia mendapat gelar Phd, dia kembali ke Cambridge dan bekerja paruh waktu di Government Code and Cipher School di Bletchley Park. Ketika Inggris mendeklarasikan perang terhadap Jerman tahun 1939, Alan mulai bekerja fulltime disitu memecahkan kode enkripsi yang dipakai oleh Jerman selama PD 2, bersama lebih dari 10000 orang dari berbagai keahlian seperti mathematicians, engineers, linguists, dan pakar-pakar dari bidang lain. Proses dekripsi (decryption) mengkombinasikan komputasi mekanik dan elektrik dengan menggunakan teknologi yang ada pada saat itu.
Awal PD 2, Jerman menggunakan komunikasi wireless. Mereka menggunakan mesin enkripsi bernama Enigma sebelum dikirim ke kode Morse. Tiap hari, Enigma menggunakan setup mesin yang disebut sebagai 'Key'.
Alan Turing mendesain alat untuk mendekripsi kode tsb bernama BOMBE yang mensimulasikan 36 Enigma. Solusi Turing adalah berdasarkan fakta bahwa pesan-pesan militer secara rutin identik.
Kemudian Jerman membuat alat enkripsi yang lebih canggih yaitu Lorenz SZ42 yang mengenkripsi data menggunakan mesin teleprinter 5 bit. Deskripsi pesan tunggal memerlukan waktu 6 minggu. Turing terlibat dalam pengembangan alat untuk memecahkan kode yang dihasilkan oleh Lorenz.
Karena tidak mungkin membangun mesin mekanik baru untuk tiap kode enkripsi yang baru, maka para ahli di Bletchley Park berusaha membuat komputer elektronik untuk mengimplementasikan algoritma untuk memecahkan kode-kode tersebut dengan lebih cepat. Colossus Mark II dapat memecahkan kode dalam waktu sekitar 6 jam dan bisa mendekripsikan kode D-Day Invasion tgl 6 Juni 1944.
Teknologi yang dikembangkan di Bletchley Park tetap menjadi top secret setelah perang. Turing dan teman-teman kembali ke dunia akademik dan akhirnya mereka mulai mengembangkan komputer elektronik untuk keperluan umum. Bletchley Park adalah tempat kelahiran bagi modern computer science. Tempat yang wajib dikunjungi oleh para computer scientist.
General purpose computers yang dibuat setelah PD 2 :
Manchester Baby, Ferranti Mark I, Harvard Mark I, US Army ENIAC.
Post War (1950) :
- Ilmuwan dan ahli matematika adalah pemenang perang
- Matematikawan dan ilmuwan diperlakukan seperti pemain bola yang terkenal
- Film Beautiful Mind memperkuat citra tsb, berkisah tentang :
John Forbes Nash : Phd dari Princeton th 1950 pada usia 22 tahun, seorang matematikawan di MIT th 1951-1958, seorang schizoprenia, sblmnya menciptakan game theory, mendapat hadiah nobel bidang ekonomi th 1994.
Tahun 1950an, sudah ada komputer berukuran besar seperti 25 kulkas, sudah menggunakan modem untuk koneksi yang masih sangat mahal, sehingga sering hanya dipakai untuk local calls. Pada tahun 1960an, long distance calls sangat mahal, merupakan barang mewah.
Phone line networking :
- dial up acces :
* could call other computer long distance
* the charcacter were encoded as sound
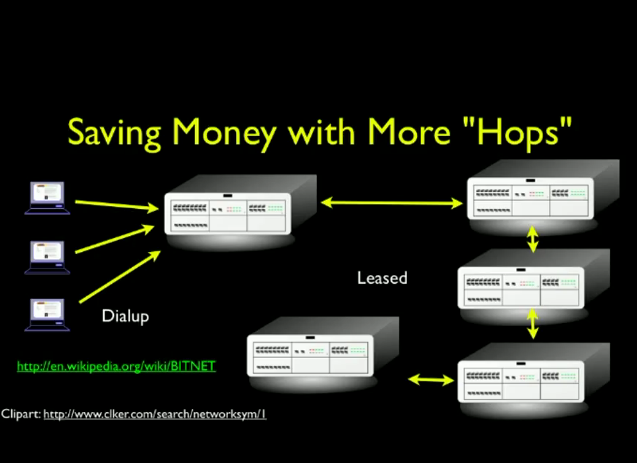
-leased lines: contract to phone company to use some of the copper intheir plant. Typically used for banks.
*get a dedicated connection between two points from the phone company
* no dealing was needed, leased lines are always connected
* reserved dedicated phone wires and permanent connection
* expensive because of limited copper - cost was based on distance
* think bank branch offices and other places where cost is significant
Awal 80an : networking untuk mengirim email, email sampai ke negara lain dalam 6 jam sampai 2 hari (Bitnet). Digunakan oleh Universitas yang bergabung bersama sehingga biaya lebih murah.
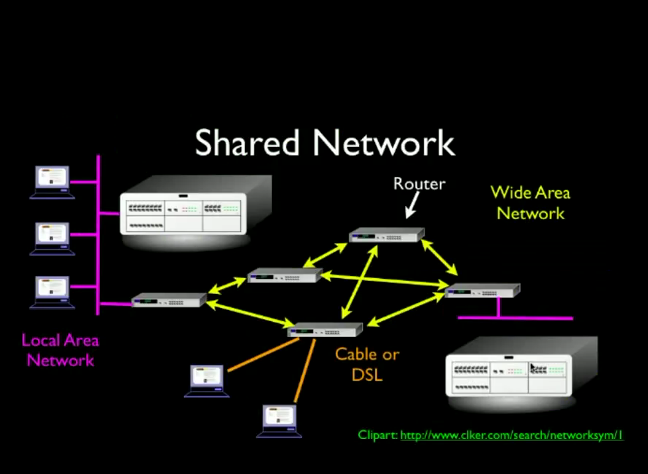
Defense Advanced Research Projects Administration (DARPA) melakukan riset tentang bagaimana agar message dapat dikirim lebih cepat.
Packet SWitching : break each message into small parts (packets), each part can flow over different paths, using special-purpose computers called routers for the traffic control --> memungkinkan beberapa message dikirim secara simultan dan sebuah message yang panjang tidak memenuhi jaringan. Router tidak menyimpan data untuk jangka waktu yang lama, dan hanya menyimpan data berukuran kecil.
Karena reset yang makin berkembang, beberapa Universitas perlu membeli superkomputer yang ukurannya besar. National Science Foundationmenyarankan untuk membeli sedikit superkomputer dan membangun national shared network.
Resources :
Unit 0: Course OverviewWelcome: Part I & IIUnit 1: History - Dawn of Early Computing (1940 - 1960)History Through Bletchley Park and Computing in WWIIHistory through Modems and TerminalsFurther reading- Turner, Fred. 2006. From Counterculture to Cyberculture: Stewart Brand, the Whole Earth Network and the Rise of Digital Utopianism. Chicago University Press.
- Standage, Tom. 2007. The Victorian Internet: The Remarkable Story of the Telegraph and the Nineteenth Century’s On-line Pioneers. Walker.
- Singh, Simon. 1999. The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography. Doubleday.
Week 1 Quiz
This is the week 1 quiz. The goal of this quiz is to help you learn. You can take the quiz multiple times and the high score will be kept. You can discuss the quiz questions with your fellow students even while you are taking the quiz.
Question 1
What was the Lorenz Machine used to transmit?
Long strategic messages with lots of detail
Intelligence between the American and British forces
Detailed information between Hitler and his Generals
Personal messages from soldiers back to their families and friends
News stories from Germany to the soldiers at the front so they would feel more connected to family and friends back home
Question 2
What did the Polish Cipher Bureau give to the British?
A Polish dessert called the Bomba
A German Geheimschreiber
Access to the Polish telephone network data transmissions
A technique for breaking encoded German Enigma messages
Question 3
What was the mistake made by the German Enigma operators that allowed Alan Turing to craft a strategy to break coded German messages?
They did not use upper and lower case letters in their password
Many operators would encrypt and send the same short perfunctory message day after day
They would leave the unencrypted messages on small pieces of paper and spies could sneak into their tents and take the messages.
For the first message of each day, operators would send the same message encrypted and un-encrypted making it easy to derive the decryption key
Question 4
What is a Modem used for?
Decrypt coded German war time transmissions
Insure that transmissions to submarines work even when they are deep under water
Record encrypted data from wireless transmissions for later decryption.
Retransmit lost packets so as to insure the overall reliability of Internet connections
Connect to a computer central from an office using a normal voice-based telephone line
Question 5
What are leased lines?
Secure lines used to connect British cryptographers to British military command
Dedicated telephone lines organizations paid telecom companies monthly to have continuous access to
The modern lines we connect to the internet through
Question 6On the Colossus computer what was used to store and repeatedly read the encrypted message text?
A spinning magnetic disk drive that was read like a tape
A paper tape that was read using light sensitive tubes
A solid-state flash drive (i.e. a USB stick)
Strips of film
Question 7
What made Bletchley park successful?
The information provided by the Polish Cipher Bureau
Their huge team dedicated to the purpose of decryption
The unlimited budget available to them
All of the above
Question 8
Who did the Enigma machine belong to?
The Polish
The British
The Norwegians
The Germans
Question 9
Who created the functional design of the Bombe?
Alan Turing and Gordon Welchman
Alistair Dennison and Tommy Flowers
Max Newman and William (Bill) Tutte
Question 10
Where is Bletchley Park located?
Buckinghamshire, England
New Mexico, United States
Sydney, Australia
Glasgow, Scotland



 RSS Feed
RSS Feed